Overview
Ransomware continues to be a significant source of disruption for healthcare organizations (hereafter referred to as "entities"), causing multi-week operational outages and direct impacts to patient care. Even after a healthcare entity returns to operational status, the stolen data persists.
Ransomware's impact is too often evaluated exclusively at the sector level. While this perspective may generate compelling trade-publication headlines, it conceals critical subsector risk dynamics, ultimately diluting the analytical value of the resulting conclusions.
This report describes the approach used to break the healthcare sector into meaningful subsectors, helping highlight which healthcare subsectors face the highest statistical likelihood of attack. This report is intended to serve as a blueprint for similar analyses across other sectors.
Why this Matters
Healthcare information is among the most sensitive categories of personal data. A study by the American Medical Association found that nearly 75 percent of respondents are concerned about protecting the privacy of their health information. Unlike many other forms of compromised data, medical records often contain highly sensitive information, including diagnoses, laboratory results, psychotherapy notes, and other protected clinical documentation.
This sensitivity amplifies the impact of Ransomware and extortion events against healthcare entities. When an entity refuses to pay a ransom, Ransomware Operators may publish stolen health records on Dedicated Leak Sites (DLS) to increase pressure. In one case, the Ransomware Operator Devman publicly released HIV test results that included patient names, ages, and sex (Figures 1 & 2). Devman escalated the extortion by threatening to "set up a website with a live map of where patients who tested positive for HIV live" and stating they would "spend some time" notifying family and friends of those individuals (Figure 3).
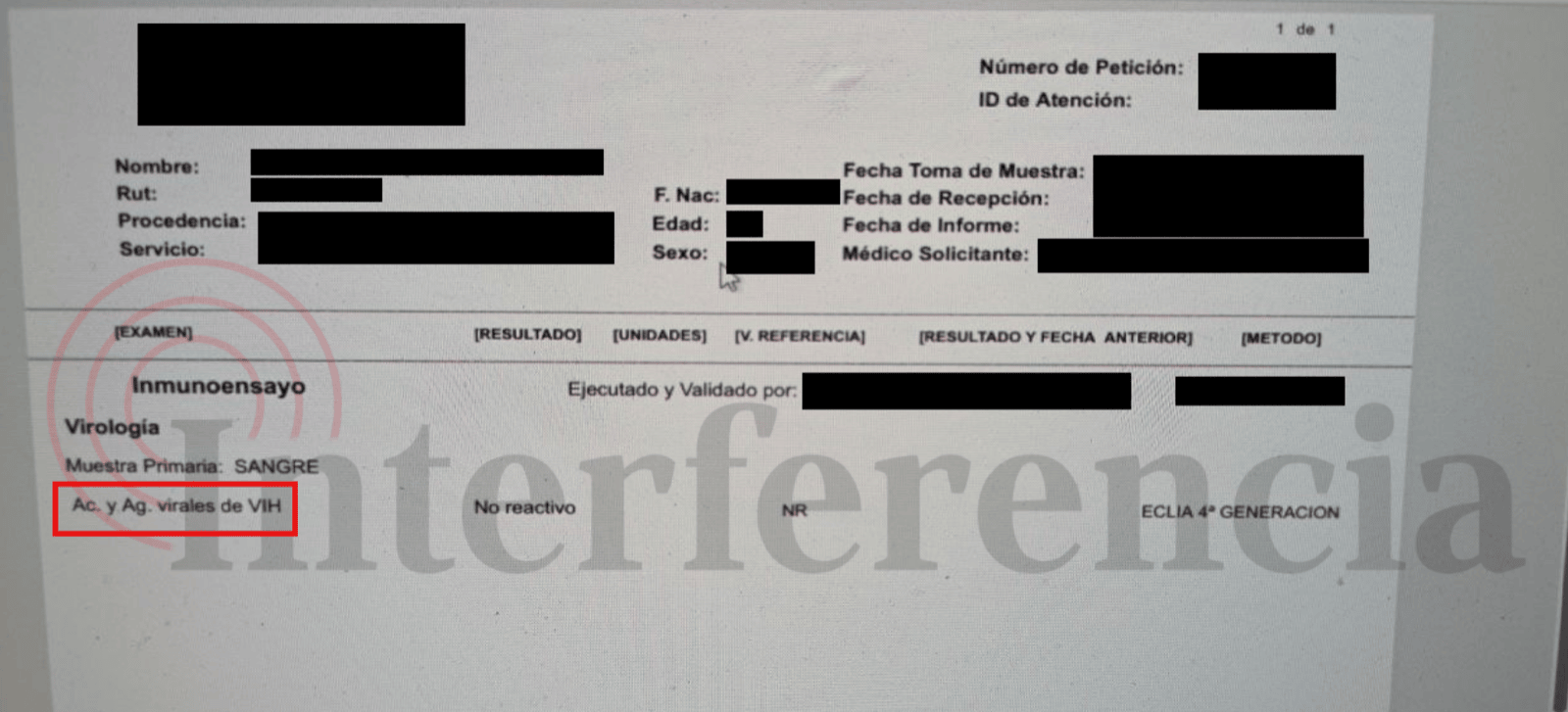
Figure 2 - File released by Devman showing HIV blood test results for a patient (note that in Spanish, HIV is translated to VIH).
Image Credit: https://interferencia.cl/articulos/tras-amenazas-por-no-pagar-rescate-hackers-publican-datos-robados-de-pacientes-de-la
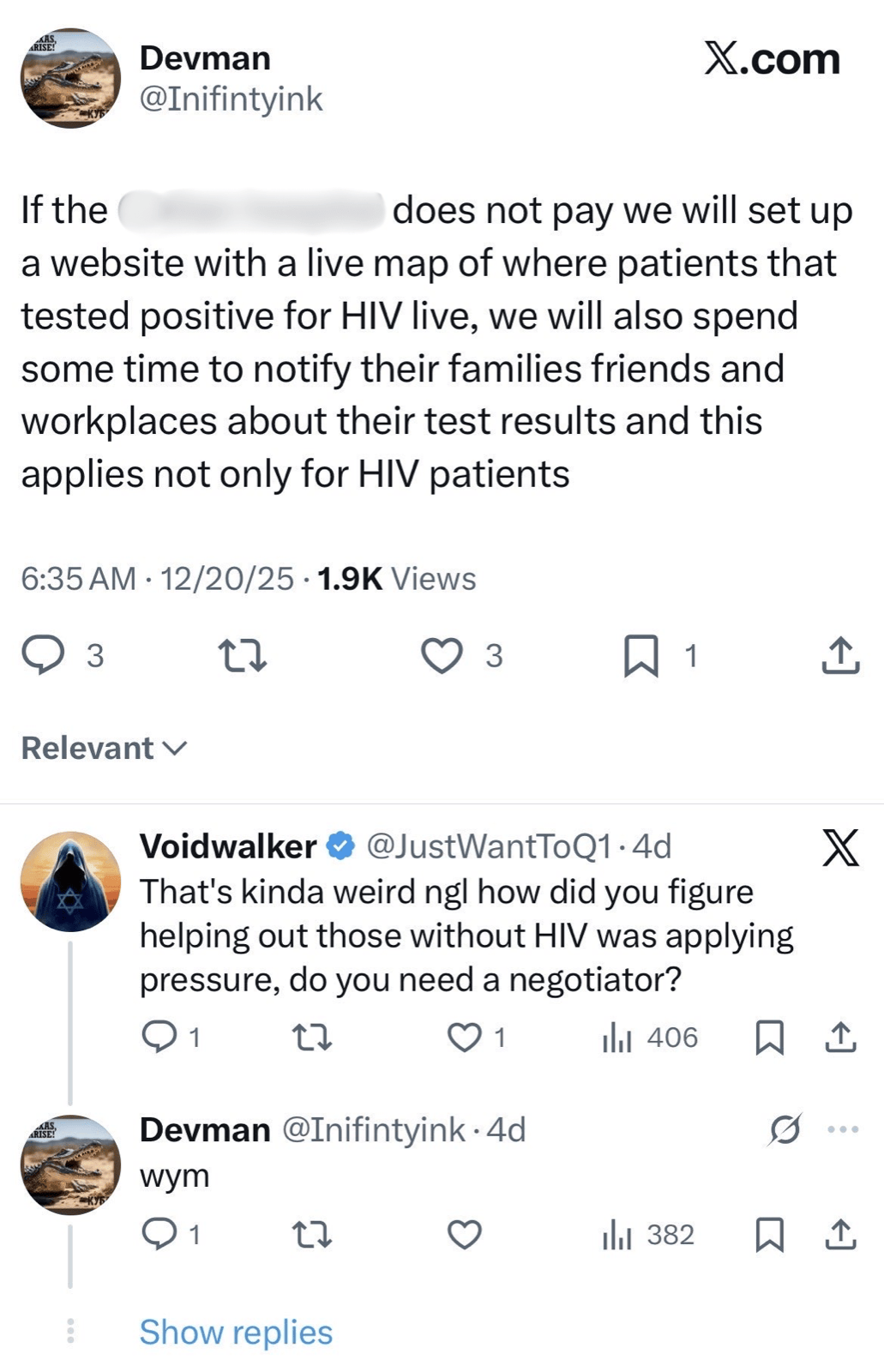
Figure 3 - X thread with Devman.
Image Credit: Katya Kandratovich
Devman also listed a nonprofit organization in a South American country focused on combating cancer (Figure 4).
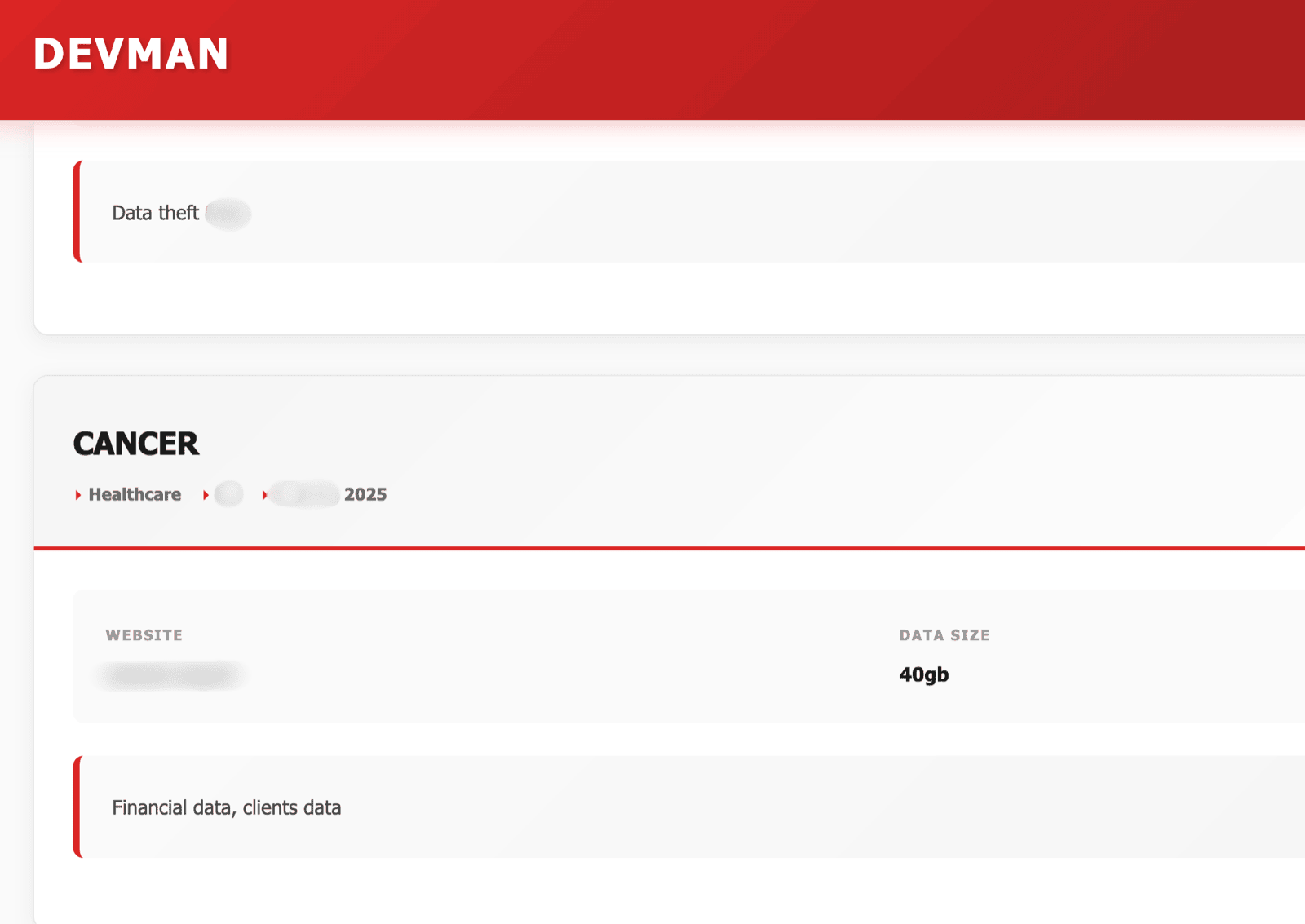
Figure 4 - DLS Post by Devman regarding the financial and client data it obtained from a non-profit organization focused on fighting cancer.
Devman has used the social media platform X (formerly Twitter) to relay their activities. Devman operates under the username @Infinityink on X and has taunted researchers, security vendors, attacked entities, and referenced their own financial gains. As Anastasia Sentsova wrote on LinkedIn, after an attack, the Operator can publicly refute an entity's claims, thereby allowing the adversary to influence public understanding of what occurred and what data is in the possession of the Operator.
In another instance, the Ransomware Operator Anubis attacked an obstetrics and gynecology practice and published clinical images containing sensitive patient anatomy. The corresponding DLS post included the caption, "The biggest leak of boobies!" (Figure 5).
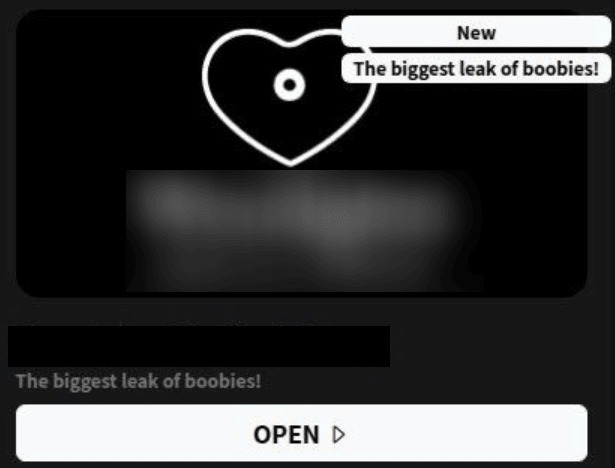
Figure 5 - Anubis DLS post which included dozens of anatomical images, some of which showed patient's faces.
These incidents demonstrate that cyberattacks against healthcare entities extend beyond operational disruption and financial loss. The exposure of sensitive medical information can lead to stigma, reputational harm, psychological distress, and lasting personal consequences for affected patients.
Methodology
I began with a dataset generously provided by the eCrime.ch team, which categorized healthcare victims using LinkedIn's Industry field. While useful as a starting point, this approach introduced classification challenges. For example, the broad Industry field of "Hospitals and Health Care" could apply equally to a small orthopedic clinic and to a Level 1 Trauma Center, masking meaningful operational and risk differences between entities.
To address this limitation, I developed a custom healthcare classification framework comprising of twenty-eight distinct subsectors in August 2024. All healthcare entities posted to DLS since January 1, 2023, were retroactively reviewed and reclassified through open-source research, entity investigation, and analysis of DLS postings. A special thanks to the sites FalconFeeds, RansomLook, and Ransomware.live.
This report analyzes 1,592 healthcare entities posted across 135 unique Dedicated Leak Sites between January 1, 2023, and December 31, 2025. If multiple Ransomware Operators posted the same healthcare entity, each instance was counted as a separate post to reflect Operator-level activity and extortion behavior. Entities were classified into subsectors according to the following criteria:
| Subsector | Description |
|---|---|
| Alternative Medicine | holistic, dispensaries, chiropractic-exclusive |
| Health Insurer and Benefit Management Platforms | medical, pharmacy, ocular, dental |
| Clinics | primary care, family care, urgent care, occupational care, outpatient specialty clinics, community health clinics, walk-in clinics, correctional healthcare |
| Dentists | family dentists, routine cleanings, cavity repair |
| Dialysis Centers | renal care for patients with kidney failure |
| Health and Human Services | EMS, community health outreach programs, provincial/state/county/city health departments, epidemiology |
| Health, Wellness and Fitness | healthy eating solutions, fitness clubs, supplements, coaching, retail health, personal care products, dietitian, injectables, body contouring, laser hair removal, skin rejuvenation |
| Healthcare Technology Monopoly | Change Healthcare, Availity, etc |
| Home Health Care Services | in-home nursing care, physical therapy, palliative care, hospice care, house call |
| Hospitals | general, teaching, children's hospitals. Due to the breadth of services offered by Hospitals, likely Clinics and Specialized Care can be included in services offered by the Hospital/Health System |
| Laboratory Services | diagnostic testing, pathology, genetic, saliva, urine, PCR |
| Medical Administration | medical coding or billing, Electronic Medical Records (EMR), Health Information Management (HIM), compliance, Clinical Documentation Improvement (CDI), Revenue Cycle Management (RCM), Cost Management, Recruiting, Connected Care Management (CCM), Scribing |
| Medical Device and Equipment Manufacturing | designing, manufacturing, and producing medical devices or medical equipment |
| Mental Health Care | psychiatry, psychology, counseling, addiction treatment, developmental or learning disabilities |
| Nursing Homes and Long-Term Care Facilities | skilled nursing facilities, assisted living facilities, residential care facilities, memory care facilities |
| Pharmaceutical | biotechnology industry, pharmaceutical/vaccine manufacturing, compounding, and clinical research |
| Pharmacy Services | inpatient and outpatient pharmacy, infusions, blood donation, medication delivery |
| Professional Organizations or Medical Universities | healthcare organizations, societies, boards, training, journals |
| Radiology and Imaging | X-ray, MRI, CT scan, ultrasound, cancer radiology |
| Rehabilitation Centers | physical, occupational, speech therapy |
| Specialized Care | cardiology, neurology, orthopedics, oncology, endocrinology, gastroenterology, obstetrics/gynecology, dermatology, pediatrics, geriatrics, sports medicine |
| Surgical Services | inpatient and outpatient surgeries, endoscopy, minimally invasive procedures, plastic surgery, Lasik, bariatric surgery, fertility treatment |
| Telemedicine Services | virtual healthcare providers and services |
Limitations
It is important to note that the vast majority of Ransomware is opportunistic. While the data presented in this report may indicate that a particular Ransomware Operator is statistically likely to attack a subsector, this may be due to other factors.
However, there are occurrences when Ransomware Operators have specifically targeted healthcare, like in 2024, the Ransomware Operator, Qilin, made the following declaration on their DLS:
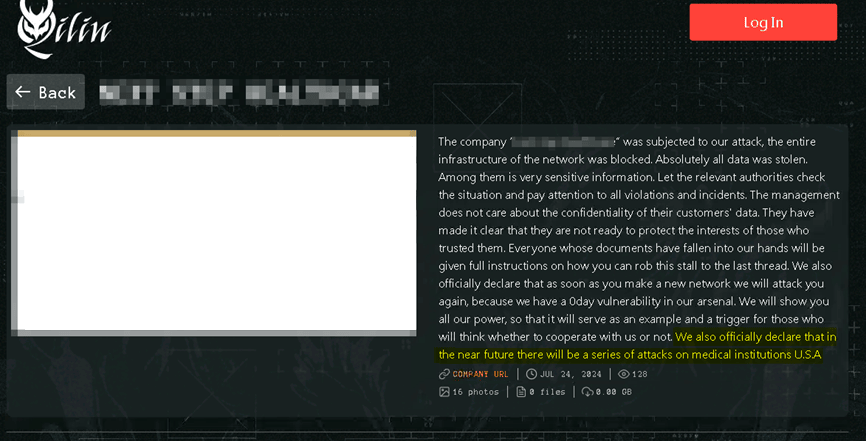
Qilin DLS declaration to attack "medical institutions".
Additionally, in 2025, Ransomware Operator Nova offered to purchase VPN access to an American or European healthcare entity with at least 500 million in revenue on the criminal forum RAMP.
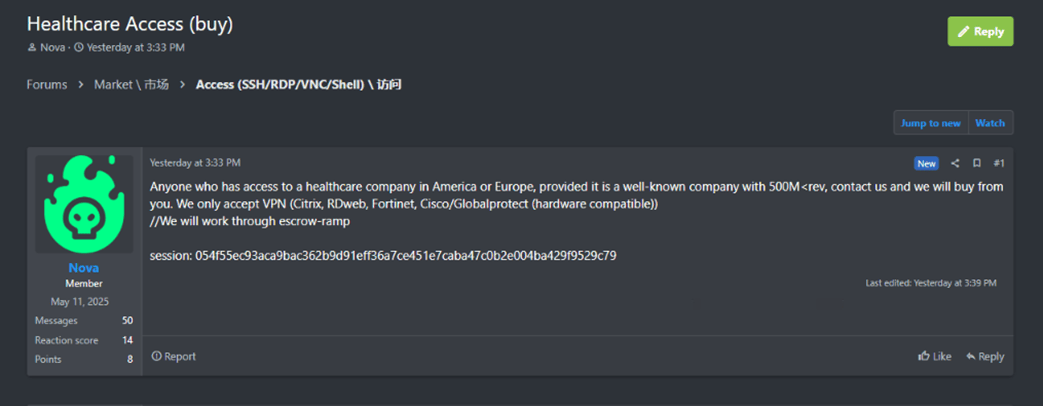
RAMP post by Ransomware Operator Nova seeking to procure initial access for a "healthcare company".
- DLS exist not only on the dark web, but also on the clear web and platforms such as Telegram. While significant efforts were taken to identify new DLS sites, the data presented should not be considered exhaustive.
- It is important to remember the statistical fallacies inherent in the data when analyzing this report. For example, the overall number of Specialized Care entities is significantly larger than that of Telemedicine Services entities, increasing the number of potential targets available to Ransomware Operators. While this does not necessarily reduce the risk of attack for Telemedicine Services entities, the data shown may indicate that Ransomware attacks occur at far fewer rates.
- Ransomware Operators may claim to have attacked an entity when a third-party provider was compromised or only one endpoint within the company was affected. It is important to remember that attribution of DLS claims is best confirmed through data breach notifications, Form 8-Ks, or transparency by the affected entities.
- A Ransomware Operator may claim to have attacked an entity on their DLS. However, due to similar entity names, they may list the incorrect URL or the entity's country of business.
- This analysis reflects entities posted on DLS; some Ransomware Operators do not maintain a DLS presence and therefore not reflected in this data.
- Ransomware-as-a-Service (RaaS) can increase the prolificacy of a particular Ransomware Operator, as more affiliates use a particular variant, leading to more postings on that DLS. This may help explain why Operators such as Qilin are the most prolific across various subsectors.
- Finally, there are Ransomware Operators no longer "in business." This could be a result of Law Enforcement intervention, desire to pursue other ventures, or absorption with another Operator.
Technical Analysis
Healthcare DLS Posts by Subsector
Specialized Care was the most frequently posted healthcare subsector on DLS from 2023 through 2025, with 2025 recording the highest number of postings observed across the three years. Mental Health Care experienced nearly a threefold increase in DLS postings over the three years, rising from 18 to 52 incidents. Hospitals recorded a 51% increase in DLS postings from 2023 to 2025, while Clinics saw pronounced growth, with postings increasing by 157% over the same period.
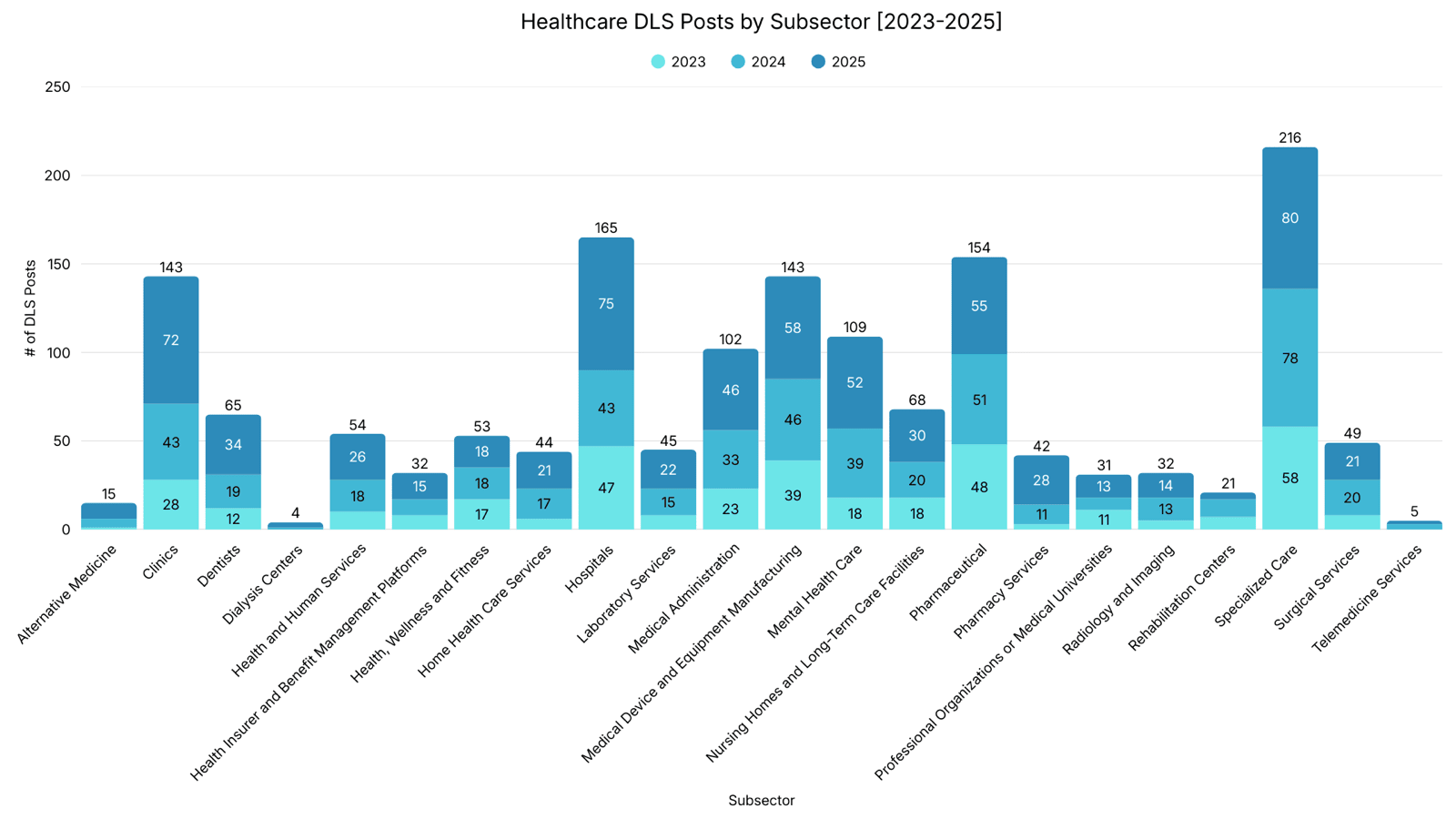
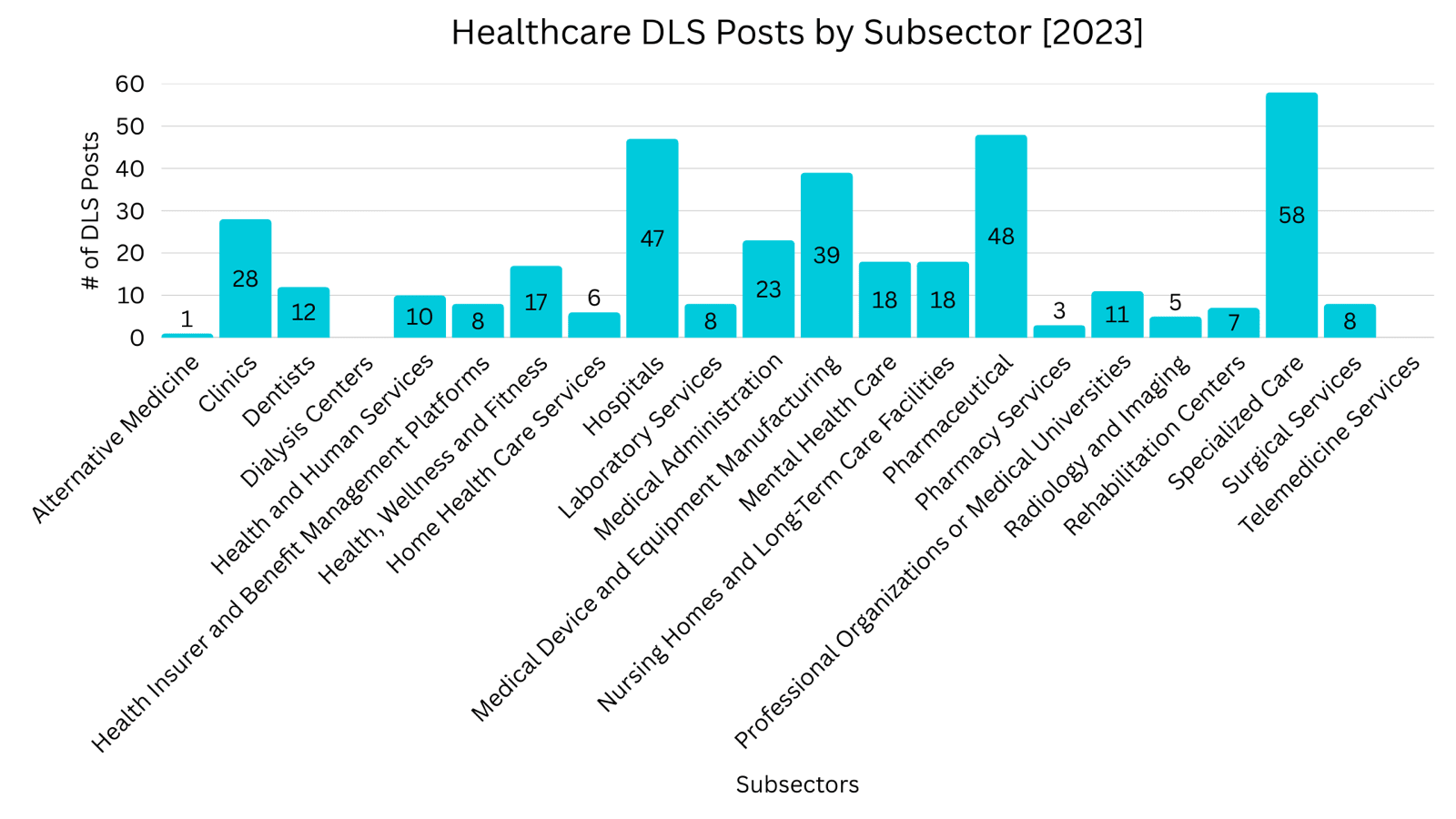
From 2023 to 2024, the most significant shift was toward smaller, specialty, and decentralized providers rather than large hospital systems. Home Health Care Services (183%), Radiology and Imaging (160%), Surgical Services (150%), and Mental Health Care (117%) saw the largest proportional increases, while Hospitals (-9%) slightly declined.
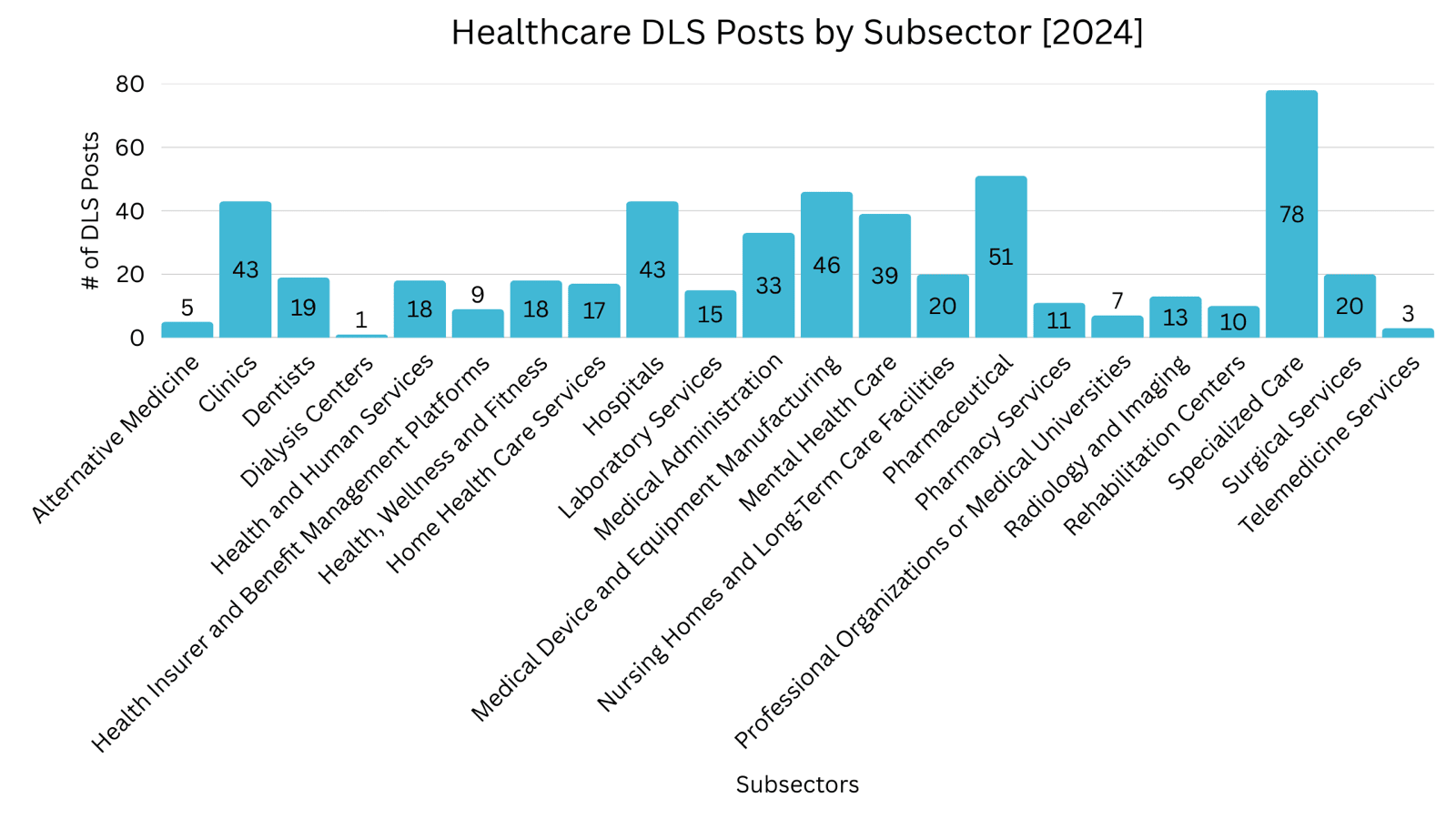
The largest increases between 2024 and 2025 occurred in Hospitals (74%), Clinics (67%), and Pharmacy Services (155%), indicating accelerating pressure on patient-facing and direct-care environments. While Specialized Care grew only 3%, it remained the most listed subsector overall. Rehabilitation Centers posts declined 60%.
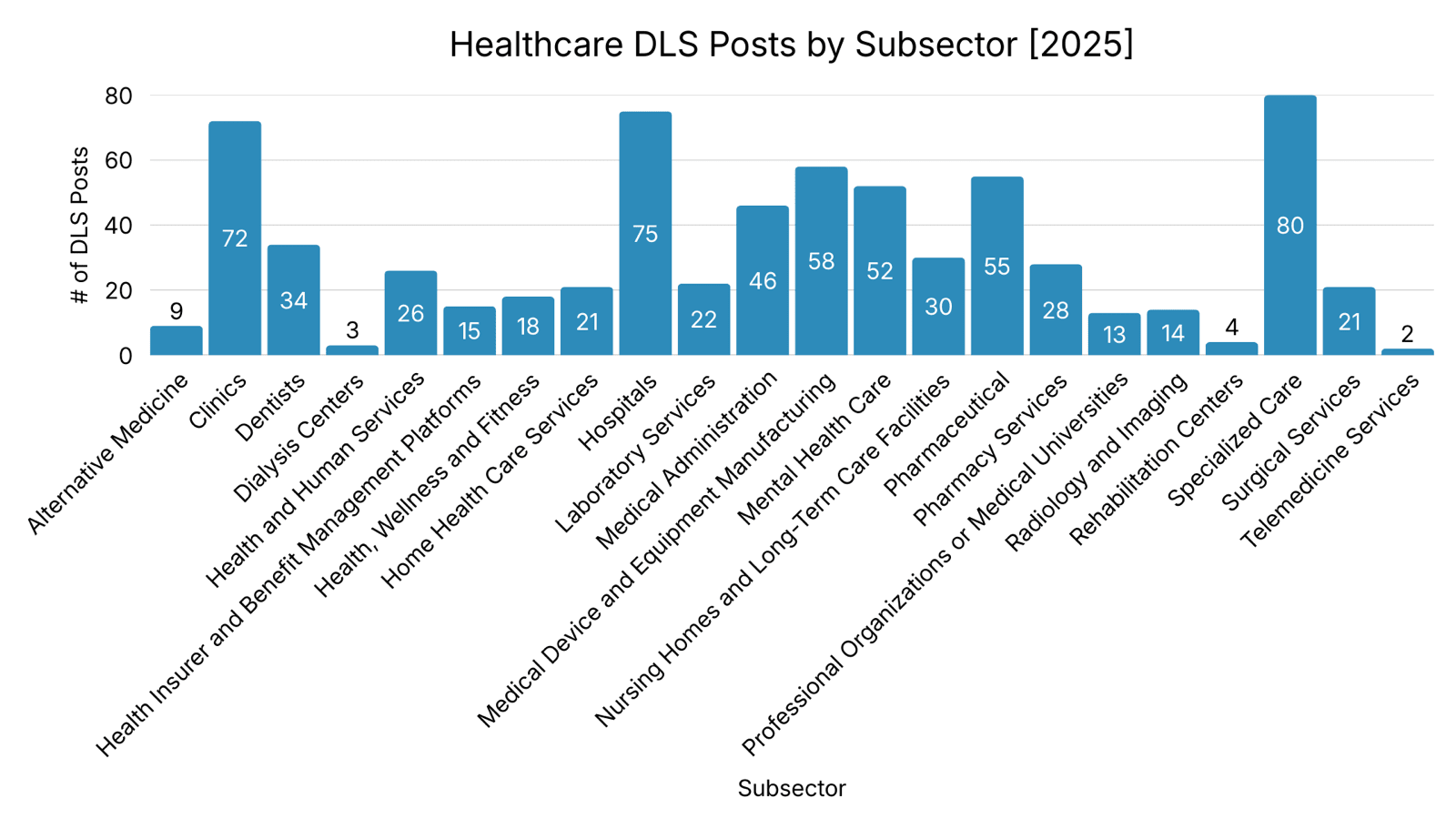
Analyst Notes: Certain healthcare subsectors may appear more frequently on DLS, in part due to their overall prevalence within the healthcare ecosystem. Subsectors such as Clinics, Specialized Care, and Dentists represent a large number of independently operated entities, increasing their likelihood of being impacted. Specialized Care in particular, encompasses a broad range of specialty providers, contributing to higher observed posts. As a result, higher representation in these subsectors should be interpreted in the context of their prevalence and size within the healthcare landscape.
Many healthcare entities, including Mental Health Care, Dentists, Specialized Care, and Nursing Homes and Long-Term Care Facilities, typically operate with small administrative teams due to their independent clinical structure. As a result, IT responsibilities are often outsourced to a managed service provider or absorbed by part-time office staff rather than by dedicated technical personnel. These environments may lack full-time security staff and formal security programs. Limited visibility, delayed patching, and inconsistent monitoring increase exposure to common intrusion techniques. These conditions may elevate exposure by providing accessible intrusion pathways and conditions conducive to extortion.
Healthcare DLS Posts by Entity Country
Country data sourced from LinkedIn
The United States accounts for the largest share of healthcare entities posted on DLS by a wide margin. DLS posts for United States healthcare entities have continued to grow, increasing by 82% from 2023 to 2025. However, there are indications of a change. Non-US healthcare DLS postings increased from 138 in 2023 to 264 in 2025, representing a 91% increase. Lastly, more than half of the countries with a healthcare entity listed on a DLS (49 of 87) recorded three or fewer healthcare DLS postings from 2023 to 2025.
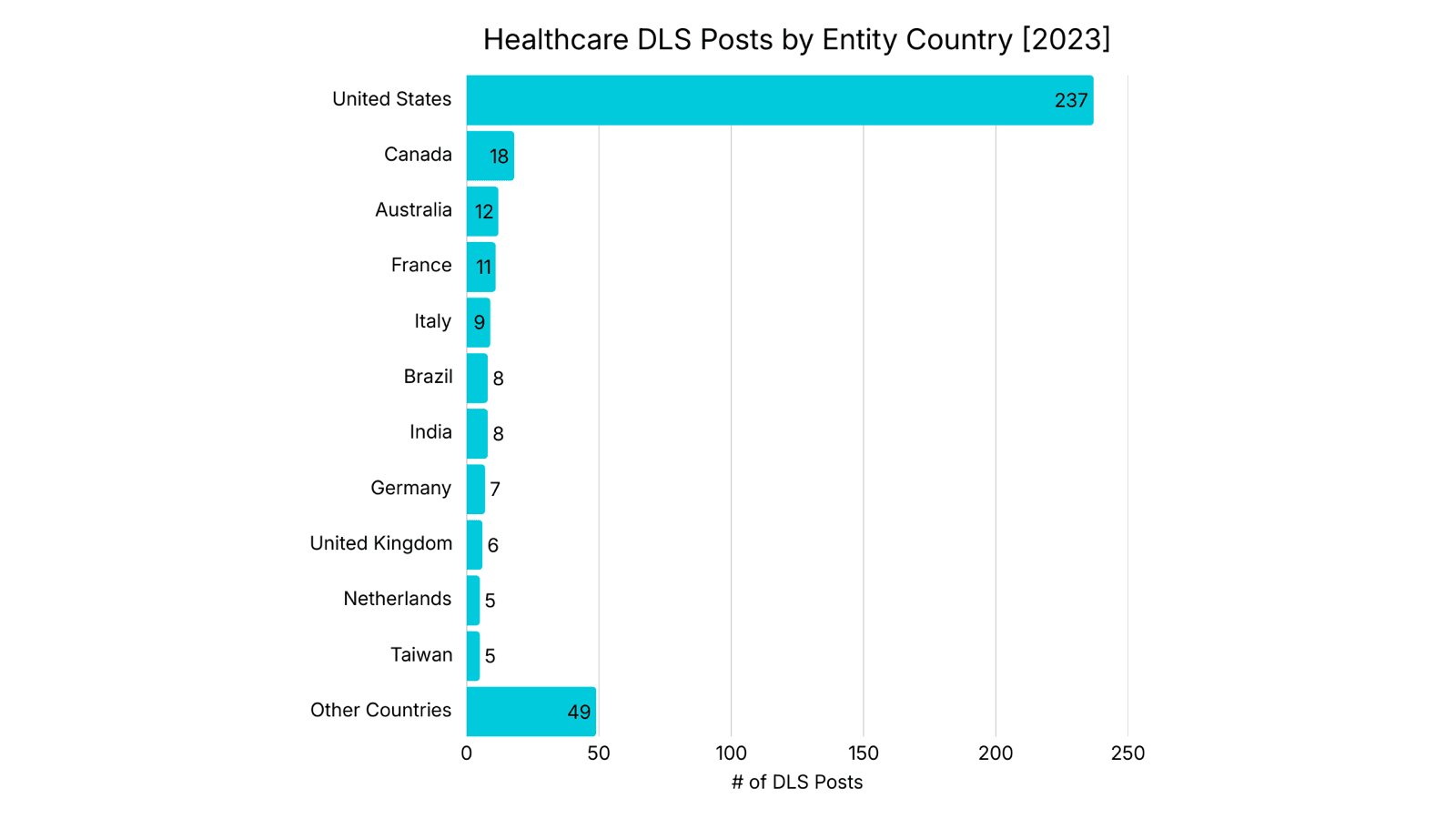
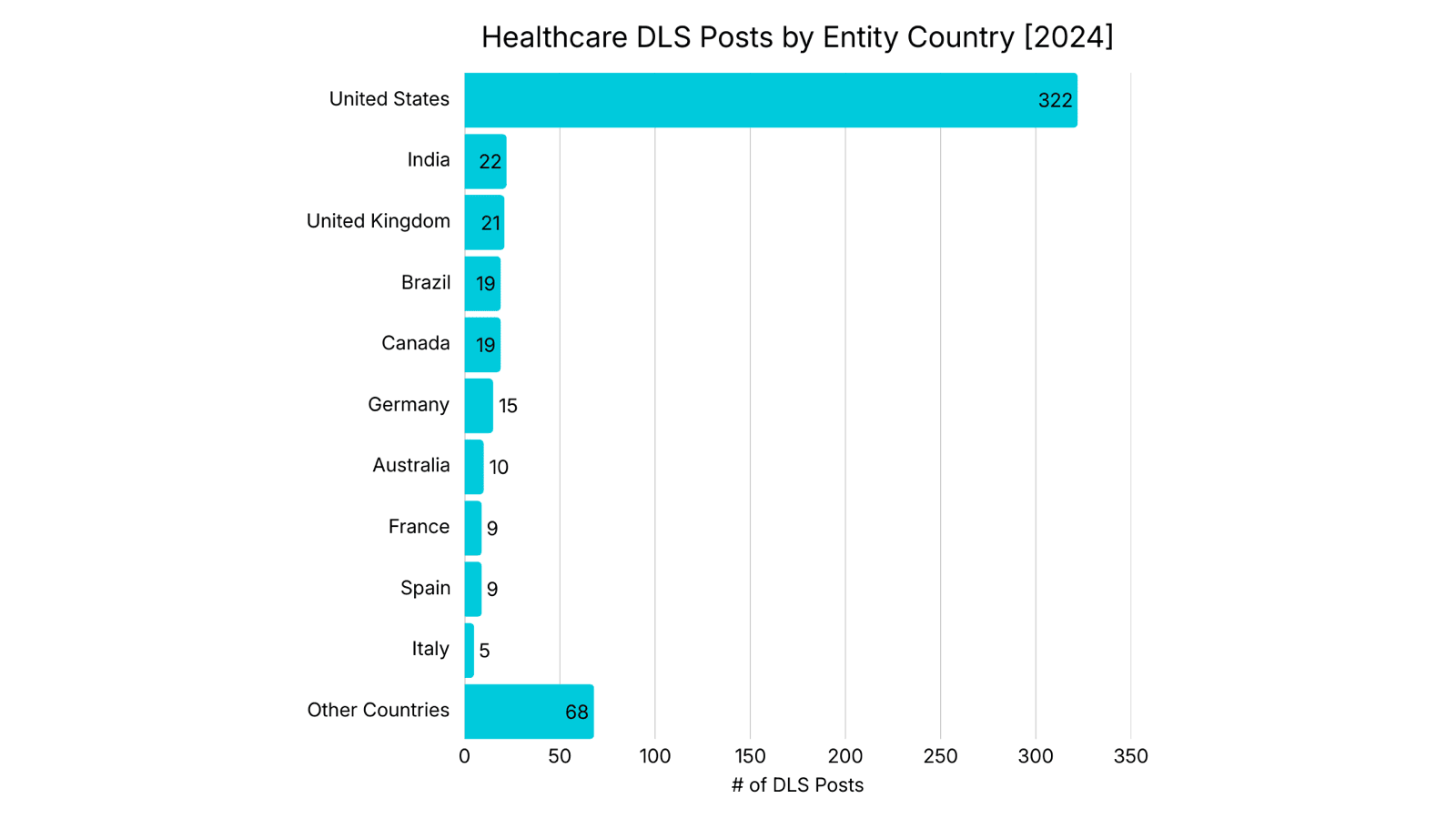
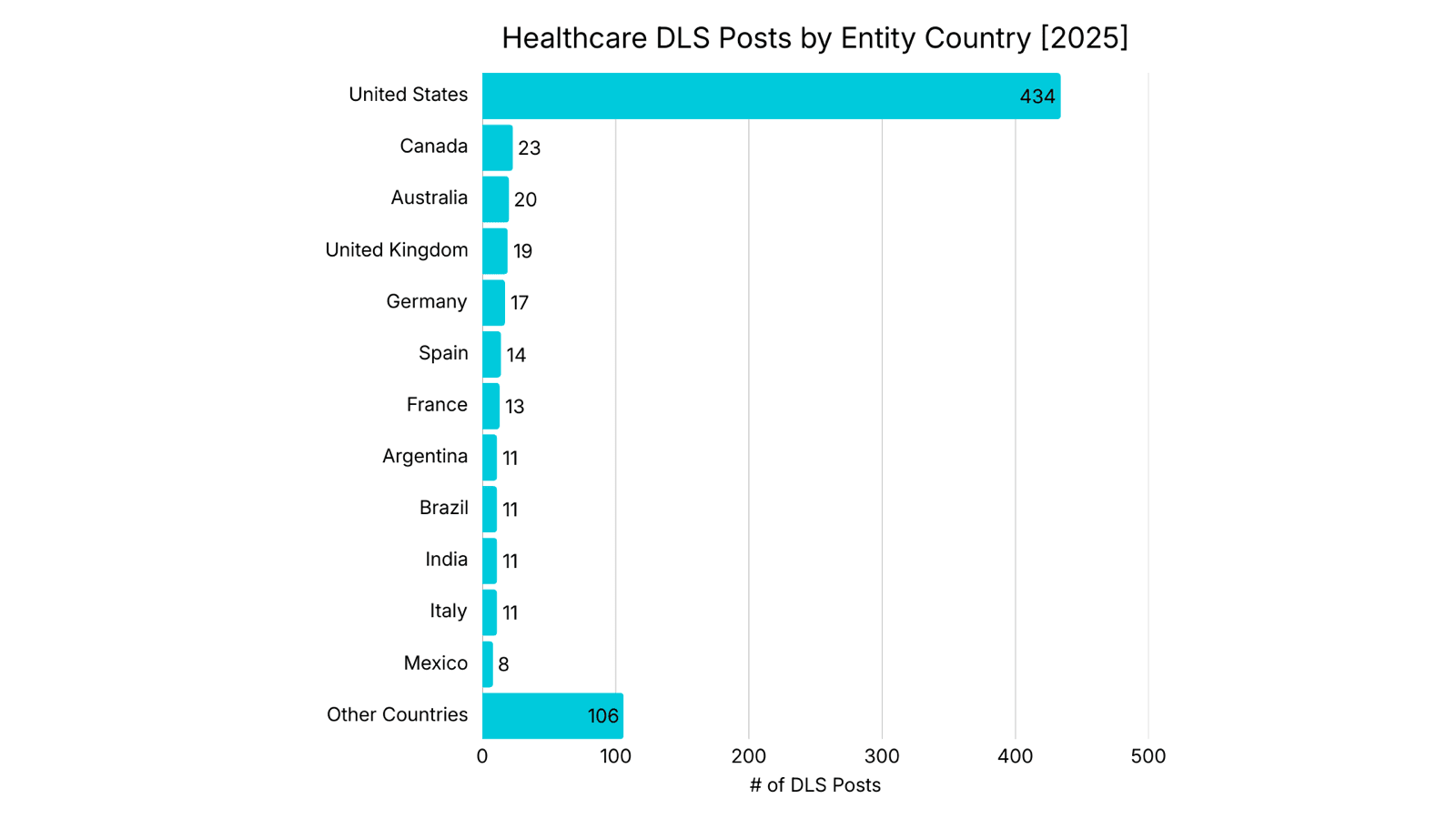
Analyst Notes: The United States has long been the primary target of Ransomware attacks, a pattern observed across sectors. Unlike more centralized models in other countries, healthcare in the United States is fragmented and privatized. This results in a larger number of individual entities serving a decentralized population, each representing a potential victim. In 2025, 71% of healthcare entities posted on DLS were in the Anglosphere. The concentration of healthcare DLS postings in Anglo-Saxon countries reflects a combination of adversary targeting preferences and structural factors. Ransomware Operators operating from CIS-linked regions have historically attacked Western healthcare systems, where operational disruption and regulatory pressure increase the leverage of extortion.
Latin American countries have observed a 263% increase in DLS postings from 2023 to 2025. Brazil (38) accounts for the majority of healthcare DLS posts over the last three years, followed by Argentina (16). Brazil maintains a hybrid public-private healthcare system and is the seventh most populous country in the world. Despite its large population, the number of healthcare entities appearing on DLS is lower than demographic scale alone would suggest.
Despite being the world's most populous country, India recorded only 41 healthcare DLS postings between 2023 and 2025, a total comparable to Brazil despite India's significantly larger population. Some Ransomware Operators prohibit their members from attacking BRICS countries, which may also explain the underrepresentation of DLS postings against healthcare entities in India, China, and Indonesia. This remains speculative and cannot be confirmed solely through DLS data.
Lastly, Healthcare entities in low-GDP countries may be less attractive due to their perceived inability to pay ransom, which may contribute to lower representation on DLS rather than to a smaller attack surface.
Healthcare DLS Posts by Entity Employee Count
Employee Count data sourced from LinkedIn; N/A represents healthcare entities without a LinkedIn company page.
For healthcare entities posted on DLS with known employee counts, entities employing 200 people or fewer represented the majority of healthcare DLS posts since 2023. The number of employees with an unknown employee count (marked N/A) increased by 235% from 2024 to 2025. These companies tend to be smaller healthcare entities and the most common subsectors were Specialized Care, Clinics, and Dentists.
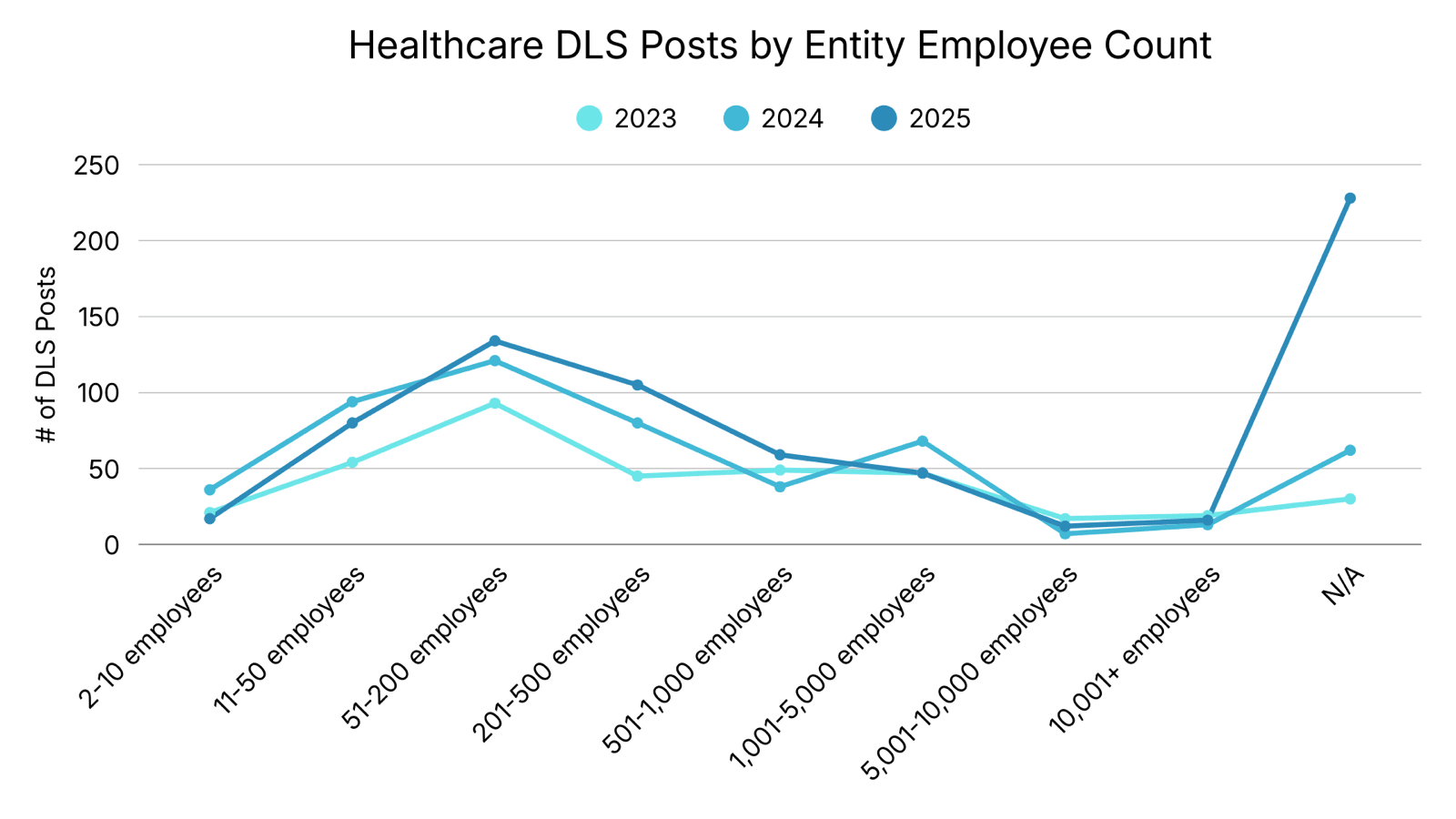
Analyst Notes: Healthcare entities with fewer than 200 employees may often rely on outsourced IT services, which may limit visibility into internal security. In these environments, security monitoring and prevention are often deprioritized in favor of operational support, increasing the likelihood that malicious activity goes undetected until a disruptive event.
Although larger healthcare entities (1,001 employees or more) plausibly generate higher revenue and could sustain larger ransom demands, they accounted for 15% of healthcare entities appearing on DLS since 2023.
Larger entities are associated with greater security maturity and incident response capabilities, which make them more likely to detect attacks in the early stages of the kill chain. However, if a larger healthcare entity is attacked and disrupted, the impact on patient care can be more pronounced. This is especially true in critical subsectors like Dialysis Centers, Hospitals, or Healthcare Technology Monopoly, where disruptions can cascade across multiple facilities and patient populations.
Share of DLS Posts Attributed to Healthcare by Ransomware Operator in 2025
Includes Ransomware Operators with 10 or more healthcare DLS posts. Unidentifiable or obfuscated entities were not included in the denominator of an Operator's total DLS post count.
Three Ransomware Operators, Anubis, Devman, and Space Bears, derive 20% or more of their total DLS postings from healthcare entities. Despite this high sector concentration, these Operators collectively account for only 5% of all healthcare-related DLS posts, reflecting their relatively limited overall scale. In contrast, Qilin and INC Ransom together are responsible for approximately 25% of healthcare entity postings. INC Ransom stands out by combining scale and sector focus, with healthcare comprising over 18% of its DLS activity, compared to Qilin, where healthcare accounts for just over 10%. Akira and CL0P are an anomaly: together across sectors, they posted almost 1,200 entities on their DLS, with healthcare entities accounting for approximately 3%.
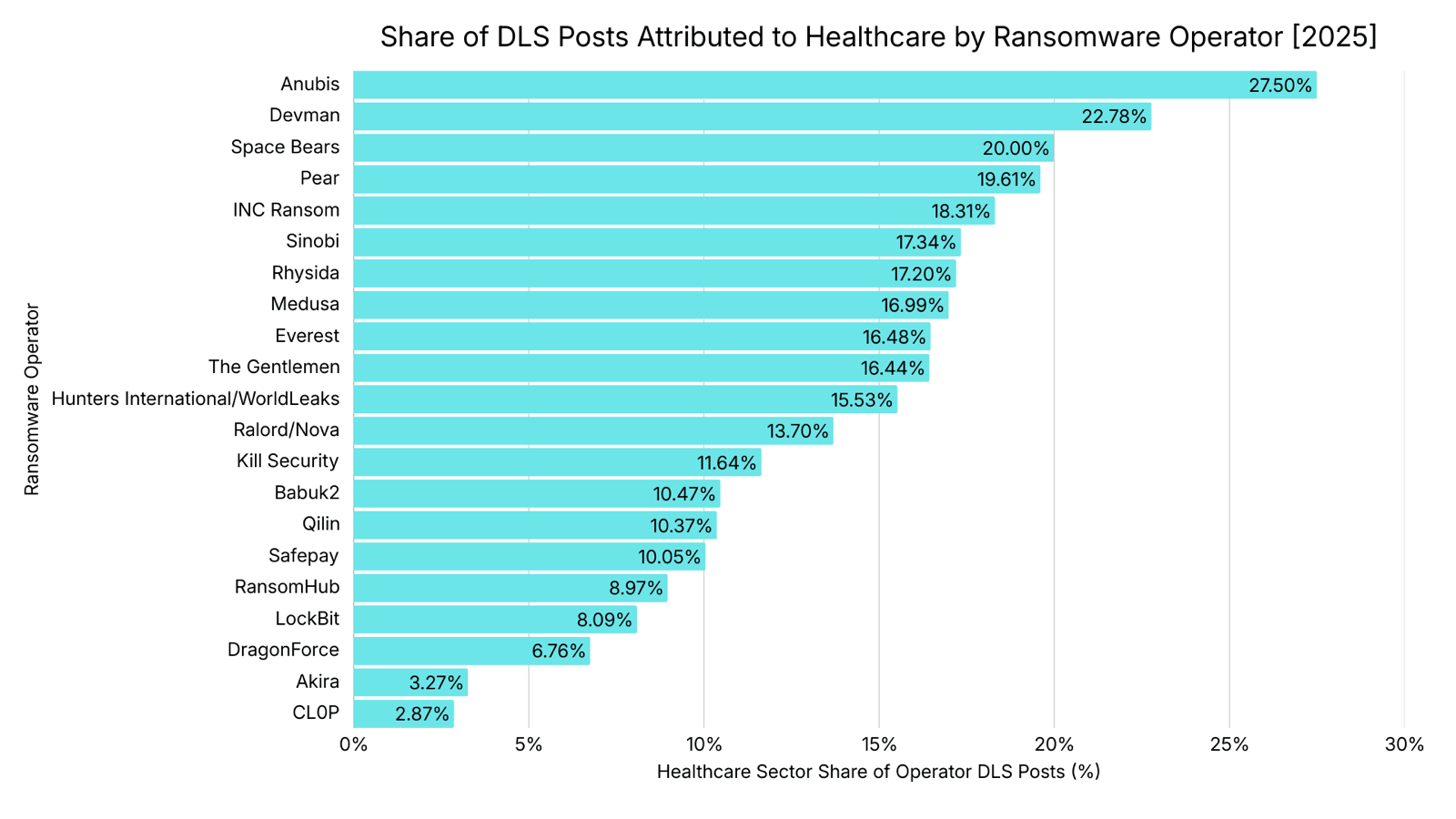
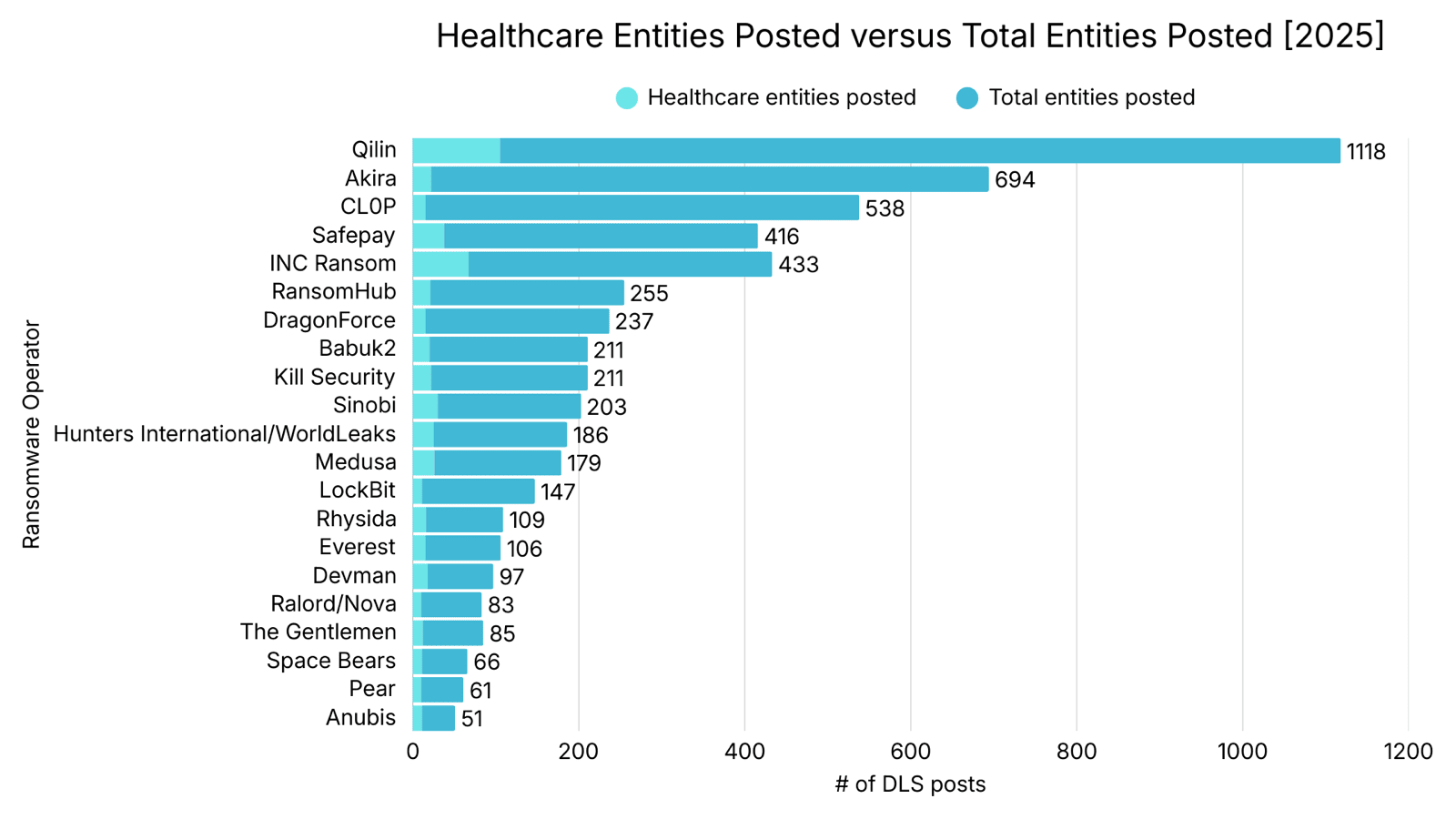
Analyst Notes: Smaller Ransomware Operators, in terms of total DLS posts like Anubis, Pear¹, SpaceBears, and Devman, consistently list healthcare entities on their DLS. While direct targeting cannot be conclusively established without additional evidence, their operations suggest a relative comfort with attacking healthcare entities. Notably, these Operators do not appear to focus on a narrow subset of healthcare entities. Across their combined 46 healthcare DLS posts, 13 distinct subsectors are represented.
Akira and CL0P exhibit notably low healthcare posting volume, suggesting deliberate avoidance rather than a lack of capability. CL0P's limited healthcare posting may be partially explained by its historical reliance on exploiting novel, high-impact vulnerabilities for initial access. These vulnerabilities disproportionately affected sectors such as Manufacturing and Professional Services, which may be more likely to deploy the vulnerable software, thereby reducing exposure for healthcare entities.
Akira's comparatively low volume of healthcare-related postings suggests potential sector avoidance, although alternative explanations, such as entity selection methods or entity acquisition channels, cannot be ruled out. Some Ransomware Operators impose internal restrictions that discourage or prohibit affiliates from attacking healthcare entities, citing moral considerations, reputational risk, or a desire to limit law enforcement scrutiny. Among the 22 healthcare entities Akira posted in 2025, approximately 82% were not directly involved in patient care. Many were for-profit entities, which are less likely to cause immediate patient harm and subsequently less likely to generate media and law enforcement attention.
Healthcare DLS Posts by Quarter [2023-2025]
Year over year, the total number of healthcare entities posted on DLS continues to increase, with an 86% rise from 2023 to 2025. The fourth quarters of 2024 and 2025 recorded the highest volume of healthcare DLS postings, while the fourth quarter of 2023 was the second-highest quarter that year. Notably, healthcare postings declined by approximately 37% from the first quarter of 2025 to the second quarter of 2025, indicating a mid-year slowdown following an early-year surge. Historically, posting volume tends to plateau between the second and third quarters.
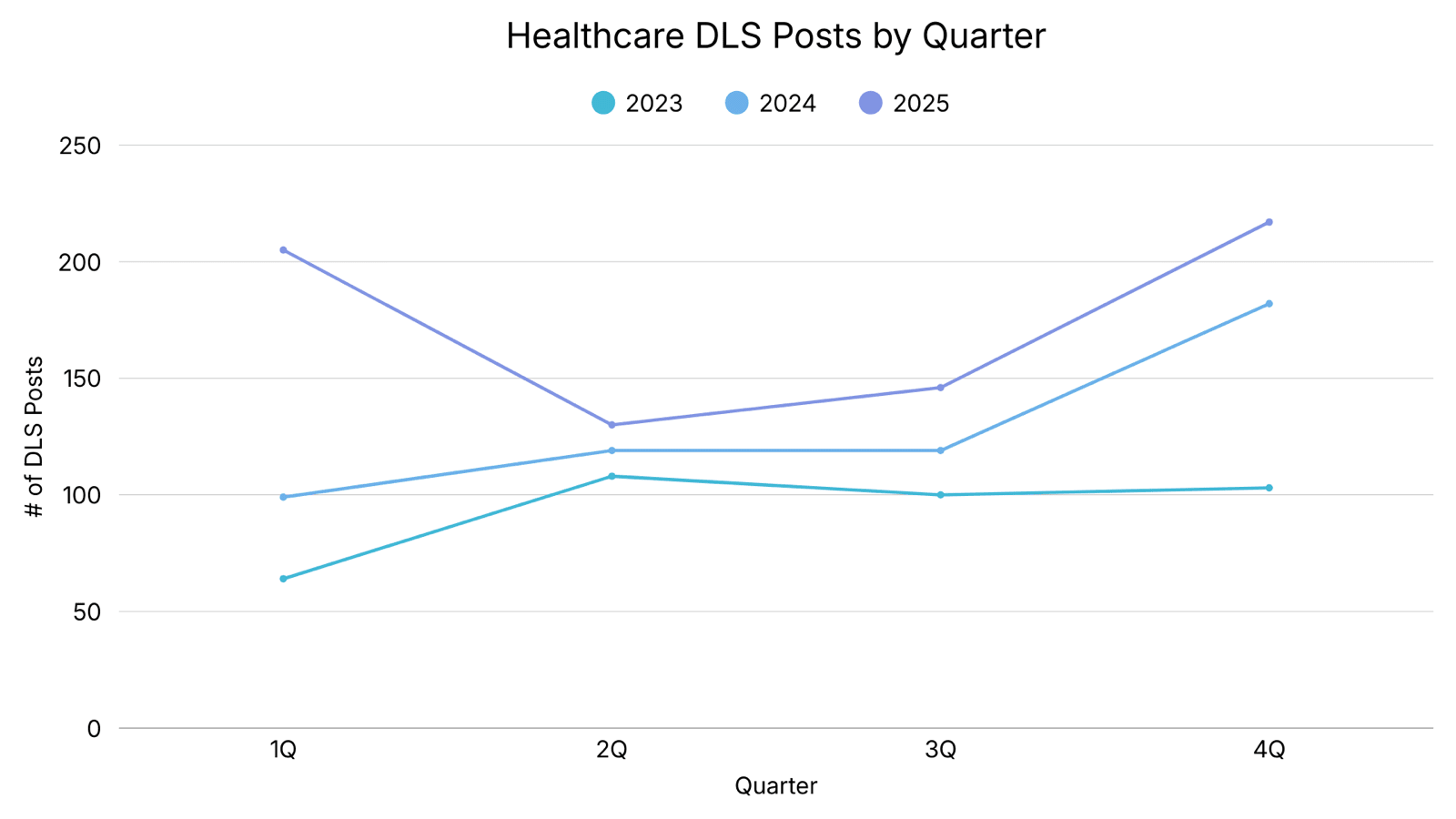
Analyst Notes: The fourth quarter coincides with major United States holiday periods, during which healthcare entities may operate with reduced staffing. Ransomware Operators may view this period as offering increased leverage due to delayed response capabilities. Additionally, as reported by Numeric, approximately 70% of Fortune 500 companies have a fiscal year-end in the fourth quarter, which may further increase pressure to resolve disruptions quickly.
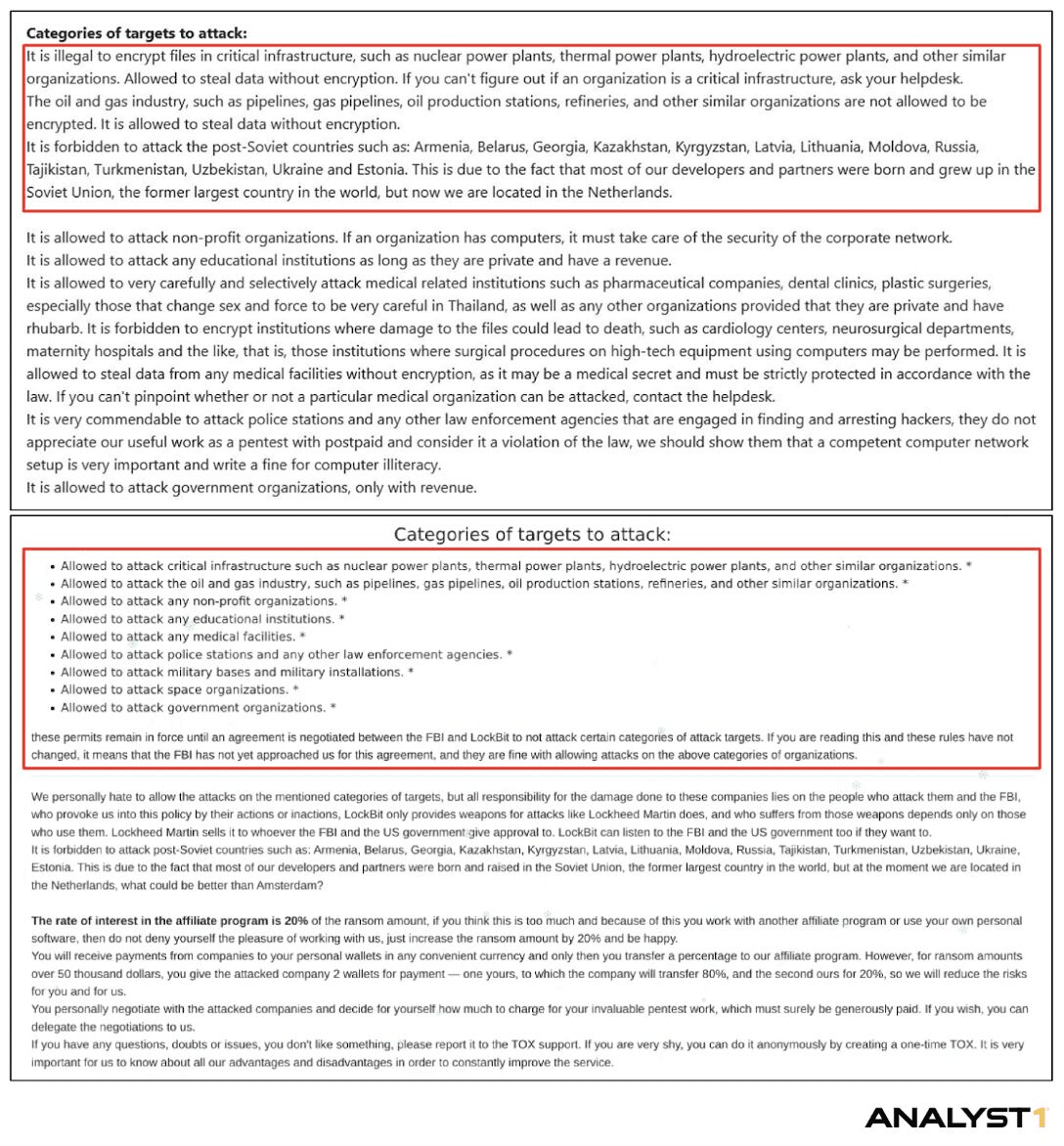
Another factor at play could be the easing of restrictions on affiliates from Ransomware Operators. Historically, some Operators have prohibited attacks against Healthcare, including Lockbit. As Anastasia Sentsova details in this reporting, Lockbit's 3.0 iteration had specific guidelines on which Medical Institutions could be attacked. In LockBit's 5.0 iteration, released in the second half of 2025, affiliates are "allowed to attack any medical facilities."
Lockbit's 3.0 (upper) and 5.0 (lower) guidelines for which categories can be attacked.
Image Credit: Analyst1 and Katya Kandratovich.
Top Ransomware Operators by Healthcare Subsector and Year
Highlights the three most prolific Ransomware Operators by healthcare subsector by year. When multiple Operators recorded the same number of postings, ties are indicated in the same cell, separated by commas. Note that some of these Operators are no longer active.
| Subsector | Year | Top Ransomware Operator #1 | Top Ransomware Operator #2 | Top Ransomware Operator #3 |
|---|---|---|---|---|
| Alternative Medicine | 2023 | Abyss (1) | — | — |
| Alternative Medicine | 2024 | Handala (1), Kill Security (1), LockBit (1), Qilin (1), Ransomcortex (1) | — | — |
| Alternative Medicine | 2025 | Qilin (2) | DragonForce (1), El Dorado/BlackLock (1), Global (1), INC Ransom (1), Miga (1), Rhysida (1), Safepay (1) | — |
| Clinics | 2023 | Karakurt (5) | LockBit (4) | AlphVM (3), BianLian (3) |
| Clinics | 2024 | INC Ransom (8) | BianLian (6), RansomHub (6) | LockBit (5) |
| Clinics | 2025 | INC Ransom (10) | Qilin (6) | Medusa (5), Safepay (5) |
| Dentists | 2023 | 8BASE (2), AlphVM (2), LockBit (2) | BianLian (1), CL0P (1), Medusa (1), Money Message (1), Monti (1), Ransomed (1) | — |
| Dentists | 2024 | Everest (4) | Qilin (3) | Mad Liberator (2) |
| Dentists | 2025 | Qilin (4), Safepay (4) | MyData (3), Sinobi (3) | Beast (2), DragonForce (2), INC Ransom (2), Obscura (2), RansomHub (2), Space Bears (2), ThreeAM (2) |
| Dialysis Centers | 2023 | — | — | — |
| Dialysis Centers | 2024 | Medusa (1) | — | — |
| Dialysis Centers | 2025 | Interlock (1), Medusa (1), Sarcoma (1) | — | — |
| Health Insurer and Benefit Management Platforms | 2023 | CL0P (5) | LockBit (1), Medusa (1), Trigona (1) | — |
| Health Insurer and Benefit Management Platforms | 2024 | Kill Security (2), RansomHub (2) | Blacksuit (1), Brain Cipher (1), Everest (1), Hunters International/WorldLeaks (1), Rhysida (1) | — |
| Health Insurer and Benefit Management Platforms | 2025 | Akira (2), Kazu (2), Qilin (2) | 8BASE (1), Babuk2 (1), CL0P (1), DragonForce (1), Genesis (1), Gunra (1), Nova (1), Sarcoma (1), The Gentlemen (1) | — |
| Health and Human Services | 2023 | AlphVM (2), LockBit (2) | 8BASE (1), CUBA (1), DragonForce (1), Karakurt (1), NoEscape (1), Royal (1) | — |
| Health and Human Services | 2024 | INC Ransom (4) | LockBit (3), Rhysida (3) | AlphVM (1), Blacksuit (1), Brain Cipher (1), Cloak (1), Daixin (1), Funksec (1), Medusa (1), MyData (1) |
| Health and Human Services | 2025 | Qilin (6) | INC Ransom (3), Ralord/Nova (3) | Devman (2), Kazu (2), Medusa (2) |
| Health, Wellness and Fitness | 2023 | LockBit (6) | CL0P (3) | AlphVM (1), BianLian (1), BlackBasta (1), Cactus (1), Medusa (1), PLAY (1), RAGroup/RAWorld (1) |
| Health, Wellness and Fitness | 2024 | PLAY (3) | Qilin (2), RansomHub (2) | Akira (1), Arcus Media (1), BianLian (1), Blacksuit (1), Cicada3301 (1), DarkVault (1), DragonForce (1), Handala (1), Hunters International/WorldLeaks (1), Kill Security (1), Underground (1) |
| Health, Wellness and Fitness | 2025 | Medusa (4), Qilin (4) | Akira (2), CL0P (2), Lynx (2) | Funksec (1), INC Ransom (1), Safepay (1), Sinobi (1), The Gentlemen (1) |
| Home Health Care Services | 2023 | LockBit (2) | BianLian (1), CL0P (1), LostTrustTeam (1), NoEscape (1) | — |
| Home Health Care Services | 2024 | Everest (5) | Qilin (2), ThreeAM (2) | AlphVM (1), Arcus Media (1), Blacksuit (1), Dispossessor (1), Kill Security (1), LockBit (1), RansomHub (1), Rhysida (1) |
| Home Health Care Services | 2025 | Qilin (4) | INC Ransom (3) | Hunters International/WorldLeaks (2) |
| Hospitals | 2023 | Rhysida (6) | AlphVM (5) | LockBit (4), RansomHouse (4) |
| Hospitals | 2024 | LockBit (12) | Kill Security (4) | Embargo (3), RansomHub (3) |
| Hospitals | 2025 | Qilin (9) | Hunters International/WorldLeaks (5), INC Ransom (5), Sinobi (5) | Babuk2 (4), Devman (4), LockBit (4) |
| Laboratory Services | 2023 | AlphVM (2) | 8BASE (1), CL0P (1), CUBA (1), Medusa (1), NoEscape (1), Nokoyawa (1) | — |
| Laboratory Services | 2024 | RansomHub (3) | BianLian (2), INC Ransom (2), LockBit (2) | Akira (1), BlackBasta (1), Blacksuit (1), Cactus (1), Fog (1), Qilin (1), RAGroup/RAWorld (1) |
| Laboratory Services | 2025 | Everest (4), Qilin (4) | Safepay (3) | Crypto24 (2) |
| Medical Administration | 2023 | CL0P (7) | LockBit (5) | 0mega (2), Karakurt (2) |
| Medical Administration | 2024 | RansomHub (10) | BianLian (4) | Everest (3), Kill Security (3) |
| Medical Administration | 2025 | Qilin (7) | Kill Security (6) | Hunters International/WorldLeaks (4) |
| Medical Device and Equipment Manufacturing | 2023 | LockBit (7) | AlphVM (4), BianLian (4), Royal (4) | 8BASE (2), Qilin (2), Snatch (2) |
| Medical Device and Equipment Manufacturing | 2024 | Hunters International/WorldLeaks (7) | RansomHub (5) | BlackBasta (3), Cactus (3), INC Ransom (3) |
| Medical Device and Equipment Manufacturing | 2025 | Qilin (7) | Akira (6) | CL0P (5) |
| Mental Health Care | 2023 | LockBit (8) | AlphVM (3) | CL0P (2), DragonForce (2) |
| Mental Health Care | 2024 | INC Ransom (6) | Blacksuit (4), Hunters International/WorldLeaks (4) | Medusa (3), Qilin (3), Rhysida (3) |
| Mental Health Care | 2025 | INC Ransom (13) | Qilin (6) | Sinobi (5) |
| Nursing Homes and Long-Term Care Facilities | 2023 | AlphVM (3) | Karakurt (2), NoEscape (2), Royal (2) | BianLian (1), BlackByte (1), Cactus (1), CiphBit (1), Hunters International/WorldLeaks (1), Medusa (1), MedusaLocker/Ransomware Blog (1), Qilin (1), ThreeAM (1) |
| Nursing Homes and Long-Term Care Facilities | 2024 | Blacksuit (3), INC Ransom (3) | Abyss (2), LockBit (2) | AlphVM (1), Cloak (1), Hunters International/WorldLeaks (1), Kill Security (1), RansomHouse (1), RansomHub (1), Rhysida (1), Stormous (1), Termite (1), ThreeAM (1) |
| Nursing Homes and Long-Term Care Facilities | 2025 | Qilin (5), Safepay (5) | INC Ransom (4), RansomHub (4) | Hunters International/WorldLeaks (3) |
| Pharmaceutical | 2023 | AlphVM (10) | CL0P (7) | LockBit (5) |
| Pharmaceutical | 2024 | LockBit (7) | Hunters International/WorldLeaks (4), RansomHouse (4) | INC Ransom (3), Medusa (3), RansomHub (3) |
| Pharmaceutical | 2025 | Qilin (7) | INC Ransom (5) | Akira (4), Hunters International/WorldLeaks (4) |
| Pharmacy Services | 2023 | Medusa (2) | Akira (1), CL0P (1) | — |
| Pharmacy Services | 2024 | RansomHub (4) | INC Ransom (2) | Apos Security (1), Argonauts Group (1), Eraleignews/APT73/BASHE (1), Fog (1), Kill Security (1) |
| Pharmacy Services | 2025 | Qilin (4) | Akira (2), Babuk2 (2), Devman (2), Frag (2) | Arcus Media (1), Beast (1), CL0P (1), DragonForce (1), Global (1), Hunters International/WorldLeaks (1), INC Ransom (1), Kairos (1), Kill Security (1), Medusa (1), Payouts King (1), Scattered Lapsus$ Hunters (1), Space Bears (1), The Gentlemen (1), VanHelsing (1) |
| Professional Organizations or Medical Universities | 2023 | Snatch (3) | CL0P (2), Nokoyawa (2) | AlphVM (1), LockBit (1), Medusa (1) |
| Professional Organizations or Medical Universities | 2024 | Medusa (2) | Helldown (1), INC Ransom (1), Interlock (1), Kill Security (1), RansomHub (1) | — |
| Professional Organizations or Medical Universities | 2025 | Qilin (5) | Akira (1), Babuk2 (1), DragonForce (1), INC Ransom (1), LockBit (1), Medusa (1), Ralord/Nova (1), RansomHub (1), Sinobi (1) | — |
| Radiology and Imaging | 2023 | Abyss (1), AvosLocker (1), BianLian (1), Karakurt (1), LockBit (1) | — | — |
| Radiology and Imaging | 2024 | Everest (3), LockBit (3) | 8BASE (1), Dragon (1), INC Ransom (1), Medusa (1), Qilin (1), Stormous (1), WikiLeaksV2 (1) | — |
| Radiology and Imaging | 2025 | Devman (3) | INC Ransom (2) | Babuk2 (1), Everest (1), Fog (1), Kazu (1), Medusa (1), Pear (1), Qilin (1), Safepay (1), Termite (1) |
| Rehabilitation Centers | 2023 | LockBit (2) | BianLian (1), HiveLeaks (1), Hunters International/WorldLeaks (1), RansomHouse (1), Rhysida (1) | — |
| Rehabilitation Centers | 2024 | Qilin (2), RansomHub (2), Rhysida (2) | Hunters International/WorldLeaks (1), Kairos (1), MEOW (1), RansomHouse (1) | — |
| Rehabilitation Centers | 2025 | Safepay (2) | Interlock (1), Qilin (1) | — |
| Specialized Care | 2023 | LockBit (16) | AlphVM (7), BianLian (7) | 8BASE (5) |
| Specialized Care | 2024 | BianLian (15) | INC Ransom (9) | RansomHub (7) |
| Specialized Care | 2025 | Qilin (17) | INC Ransom (7) | Sinobi (5) |
| Surgical Services | 2023 | 8BASE (3) | Abyss (1), AlphVM (1), BianLian (1), Hunters International/WorldLeaks (1), LockBit (1) | — |
| Surgical Services | 2024 | LockBit (3), Qiulong (3) | Blacksuit (2), Everest (2), Qilin (2) | BianLian (1), CL0P (1), Dispossessor (1), INC Ransom (1), Medusa (1), Meow (1), Ransomcortex (1), Safepay (1) |
| Surgical Services | 2025 | Qilin (4) | INC Ransom (3), Safepay (3) | Sinobi (2) |
| Telemedicine Services | 2023 | — | — | — |
| Telemedicine Services | 2024 | Kill Security (2) | RansomHub (1) | — |
| Telemedicine Services | 2025 | Babuk2 (1), Kill Security (1) | — | — |
Analyst Notes: BianLian¹ showed a pronounced subsector concentration in 2024, with nearly 50% of its DLS posts attributed to Specialized Care, totaling 15 incidents. In contrast, this pattern did not persist in 2025, when only 2 of BianLian's 7 DLS posts involved Specialized Care.
Qilin's position as the leading Ransomware Operator across several healthcare subsectors may be explained by its exceptional posting volume in 2025. Qilin's total number of healthcare-related DLS posts exceeded LockBit's 2024 healthcare entity posts by 102%. While INC Ransom ranked second in 2025 by total healthcare postings, it still recorded 45 fewer healthcare entities than Qilin.
Unlike Hospitals and Specialized Care, where Operator diversity is paired with sustained volume, Mental Health Care exhibits high operator dispersion without concentration, indicating that Ransomware activity affecting this subsector is distributed across a wide range of actors rather than driven by a small core of repeat operators.
Several Operators appear only briefly in healthcare DLS activity, posting victims for a short period before disappearing. In contrast, a smaller subset of Operators recur year over year across multiple healthcare subsectors, indicating that a limited core of repeat Operators drive sustained healthcare victimization.
Conclusion
Healthcare entities continue to experience significant impact from Ransomware, but this risk is not uniform across the sector. Certain healthcare subsectors appear more frequently on DLS, indicating a higher likelihood of Ransomware impact. While this does not always imply deliberate targeting, these subsectors face elevated risk through simple probability and exposure, driven by factors such as entity size, staffing models, technology dependence, and operational tolerance for downtime.
Entities with threat intelligence capabilities can use these findings to contextualize Ransomware risk within their specific subsector rather than relying on generalized healthcare metrics. Identifying which Ransomware Operators are statistically associated with specific subsectors enables defenders to prioritize controls, monitoring, and response planning around the tactics and tradecraft they are most likely to encounter. This prioritization can produce compounding defensive benefits across the broader Ransomware ecosystem, as tactics, techniques, and procedures (TTPs) are often shared, reused, or emulated among Operators.
Meaningful insights emerge when analysis moves deeper than high-level sector labels and instead examines subsector-level patterns. This approach reveals trends, anomalies, and recurring behaviors that are often obscured when healthcare is treated as a single monolithic category. From a threat intelligence lens, subsector analysis enables a more accurate understanding of commonalities to explain seemingly unrelated events.
References
https://www.sophos.com/en-us/blog/eeny-meeny-miny-moe-how-ransomware-operators-choose-victims
https://www.halcyon.ai/threat-group/cl0p
https://blog.bushidotoken.net/2025/02/blackbasta-leaks-lessons-from-ascension.html
¹ There is some indication that the Ransomware Operator Pear (P.E.A.R) may represent a rebrand of, or otherwise be operationally linked to, BianLian. However, because insufficient evidence exists to confirm a direct lineage, the two Operators were analyzed separately for this investigation.